Two ZTNA Weak Spots that Hackers can Exploit and How to Fix Them
Adopting a ’zero trust’ network access posture has become an important strategy for securing hybrid and cloudified enterprise networks. Officially known as Zero Trust Network Access/Architecture, the ZTNA model is really very simple. First, contextual data is used to fully vet users and devices seeking network access. Then, if a user is approved, they enter a sort of private network-for-one that gives access to the resource they need—and nothing else. This way, if trust in the user was misplaced, at least the amount of damage they can do is limited. And you’ll know if this trust was misplaced because ZTNA lets you keep an eye on users’ behavior the whole time they’re connected!
DPI to Improve ZTNA
Two Weak Spots that Can Unravel ZTNA
In theory the ZTNA model is very strong, but it is vulnerable at two critical junctures:
- At initial access authorization,
- At the establishment of a limited ‘virtual’ network through segmentation.
At both these steps, if a solution does not have sufficient network traffic visibility, its defensive capabilities will be greatly compromised. Fortunately, Next Generation Deep Packet Inspection (NG DPI) can fill this visibility gap for more vigorous and consistent ZTNA-based protection.
Let’s look at how visibility impacts ZTNA effectiveness and how NG DPI can help at these two critical points:
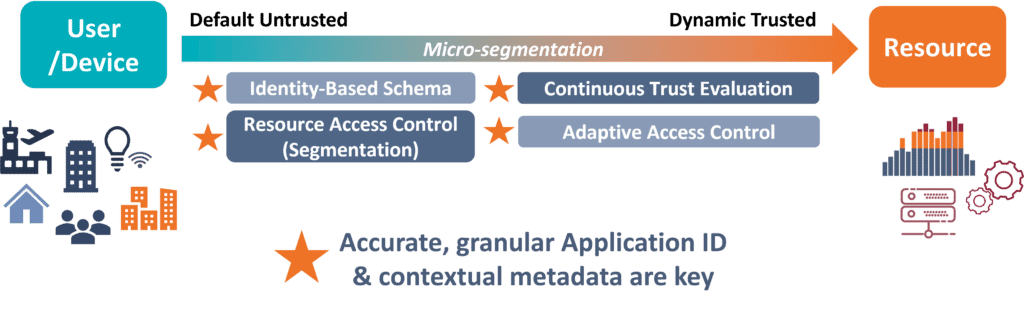
- Identity-Based Authentication: In ZTNA, simply having valid login credentials is not enough to gain access to a network. You have to go further and prove you are the legitimate owner of those credentials. Accordingly, ZTNA authenticates users (people, devices, apps, etc.) using an identity-based schema that takes context into account, such as device profiles, date and location data, and information about private applications and services. If anything is wrong or unusual, trust will not be granted.The challenge is that some of this information can be fabricated, or simply missing (like app and service info). As a result, some users who shouldn’t have access get it, and some who should are erroneously blocked. This is where NG DPI can help. It supports identity-based access by providing contextual data drawn from the most reliable source available: network-based telemetry data. And a quality NG DPI engine can also help detect threats like spoofing attacks, and the presence of rogue private applications and devices in shadow IT.
- Segmentation: Once access is granted, the goal is to provide least-privileged access to required resources. If application and service information is not granular or accurate, effective segmentation cannot be established. Here again NG DPI can help. NG DPI provides the ultra-reliable traffic classification required for segmentation, and the additional visibility NG DPI brings in the form of traffic metadata and threat indicators supports advanced micro-segmentation and traffic handling rules for enhanced security.
NG DPI also helps with continuous trust evaluation. As mentioned, in ZTNA, trust is never granted in permanence; it must be continuously earned. This is handled through continuous monitoring supported by NG DPI, which provides real-time traffic analysis that includes the identification of evasive and anomalous traffic.
Finally, NG DPI also boosts ZTNA effectiveness by supporting granular traffic monitoring that can reveal potential breaches, enabling the ZTNA solution to invoke the necessary access controls, such as rerouting or blocking traffic.
Examples of Advanced ZTNA Functions Enabled by NG DPI
- Detect and block a user trying to connect with forbidden anonymizers like Cyberghost or Ultrasurf.
- Prevent domain fronting by revealing the use of routing schemes in Content Delivery Networks (CDNs) and other services that mask the intended destination of HTTPS traffic.
- Detect and block a user trying to connect with RDP or telnet from an unusual location, or to a resource not typically accessed by RDP (traffic that might otherwise be seen as generic TCP traffic without NG DPI).
- Continuously evaluate trust by monitoring traffic to detect anomalies, such as the transfer of a file using a false MIME type (e.g., an executable masked as an image), or the presence of non-standard tunneling activities over legitimate protocols (such as DNS or ICMP), which may indicate unauthorized or illegal activities.
> To find out more how to you can use NG DPI to improve ZTNA product differentiation and innovation, I encourage you to download the industry brief: How to Improve ZTNA with Next Generation Deep Packet Inspection
> For more information on how accurate, detailed traffic and application insights delivered by Enea’s Next-Gen DPI can raise the effectiveness of ZTNA solutions: Click here
> For more about embedding NG DPI into ZTNA and wider cloud-based security solutions, you can download the technical white paper: How SSE Leaders Use Next Generation DPI for Market Success





