How to Get on the Path to Effective SASE
SASE (Secure Access Service Edge): is it marketing hype or the next wave? Is it a workable security answer to the rapidly changing corporate IT environment? Are solutions marketed as SASE today true SASE products? Or are they mostly works-in-progress? And what is “true SASE” anyway?
In this blog you will find answers to all these questions and more! I’ll explain what SASE actually is, what is driving SASE migration, what work remains for most vendors, and why there is one must-have component if you want SASE to work effectively and fulfil its many promises.
What is SASE?
First, SASE is not a technology, or even a specific architecture. It is a conceptual model. And this model has a compelling simplicity: SASE is the promise of integrated security and wide-area networking (WAN) delivered as a cloud service. This cloud service is delivered via access points around the world, enabling the fastest connections possible between workers and the IT resources they need.
Is SASE Hype or Real?
Well, to begin, the two major changes in corporate IT environments that make SASE appealing are very real:
- Applications and data have shifted to the cloud, and
- Workers are moving out of headquarter offices and into local branches, co-working spaces, home offices and coffee shops.
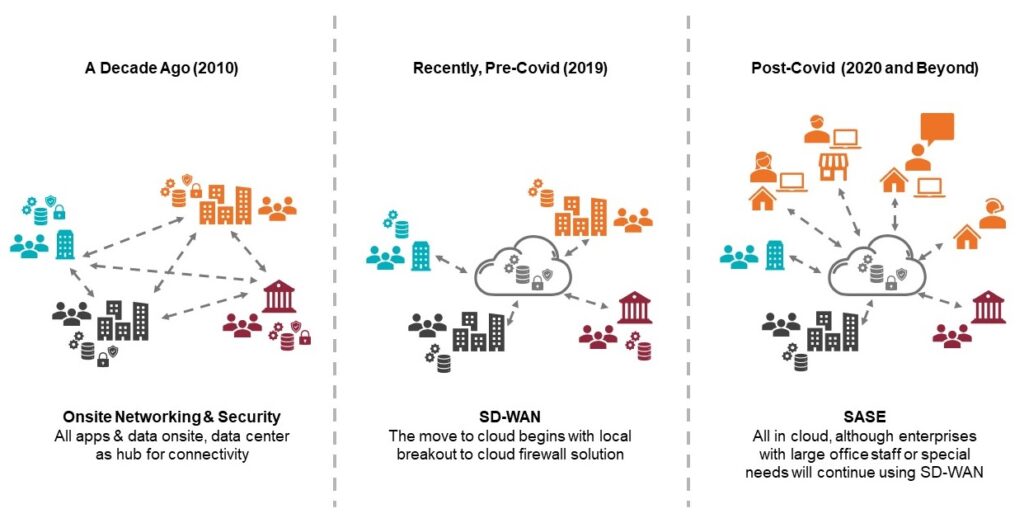
Evolution of Enterprise Network Architectures Over Time
With the advent of Covid, the shift away from onsite solutions has accelerated and the bulk of corporate traffic travels entirely outside branch offices, campus and enterprise networks. Many companies in sectors such as finance, insurance, science, technology, telecommunications, sales and services have pledged to permanently move their employees to remote working. These companies currently don’t have sufficient security or networking solutions for such an environment, and so we can expect SASE to proliferate to fill that need.
However, other segments such as healthcare, retail, manufacturing, transportation, agriculture, government and utilities have business models where their employees have to continue to work in the office. For these businesses SD-WAN will continue to fit their primary needs. And because SD-WAN has been around for about 8 years now, these companies have largely already deployed it.
But, they will still need SASE to fill connectivity and security gaps. In these industries, as in all others, the number of edge networks, including industrial IoT networks, is increasing and they need to be integrated in a way that meets their special bandwidth, latency and security requirements. Therefore, we can expect the growth, solution investments and deployments across all industries to be predominantly in the SASE area going forward. In other words, the need for and accompanying investment in SASE solutions is very real indeed.
What is “True SASE” and Where Are We Today?
In the original SASE paper, Gartner recognized that network and security architectures built upon stacks of security appliances, multi-vendor service chaining and traffic inspection via decryption and re-encryption, can’t scale. Therefore, a new solution was needed with these capabilities and features:
- A single unified, cloud security service, policy decision engine, management, provisioning and user interface (UI)
- The capability to identify sensitive data/malware
- Optimized encryption and decryption of content (e.g., using decryption selectively, and mutualizing the results of Deep Packet Inspection (DPI) across multiple services – i.e., single-pass DPI)
- Ultra-scalable, line speed data processing
- Continuous adaptive risk and trust assessment
- Distributed global Internet access Points of Presence (PoPs) for horizontal scale out
At present, there are a number of vendors whose solutions do align with the SASE concept, who do offer core capabilities like those above, and most importantly, who deliver the kind of customer benefits inherent in the SASE model.
Some of these are cloud-native SASE start-ups, some are cloud security vendors who have added SD-WAN capabilities, and others are SD-WAN vendors who have moved to the cloud and completed their offer with security services. Regardless of the development path chosen, most do still have open integration or architecture objectives in their roadmaps.
And, in terms of some of the finer points in Gartner’s definition of ‘true’ SASE, most vendors are taking a pragmatic approach and supporting specific customer needs, like maintaining hybrid environments, with on-premise SD-WAN functionality to protect investments or bolster security for critical networks. Some are also taking a measured approach to prescriptions like single-pass DPI, which requires specific engineering to address it in an optimal way. In short, it will be customer needs and vendor innovation that determine what ‘true’ SASE ultimately looks like.
Real-Time Application Awareness: The Must-Have Capability for Effective SASE
Whatever approach a vendor takes to developing a SASE offering, one capability is a must-have: real-time application awareness. This is essential for driving the key SASE functions of security, network policy and automation.

Qosmos ixEngine®, Enea’s DPI-based traffic intelligence engine, uses advanced analytics to non-intrusively extract real-time information about applications, services, content, users, devices, transactions and security from traffic flows. Developed specifically for integration into third-party applications, it provides the accurate, granular application awareness that is critical to every core SASE networking and security function, from network access to traffic steering to firewalling. And it can be flexibly deployed at the Edge, in the Data Center, or in the Cloud.
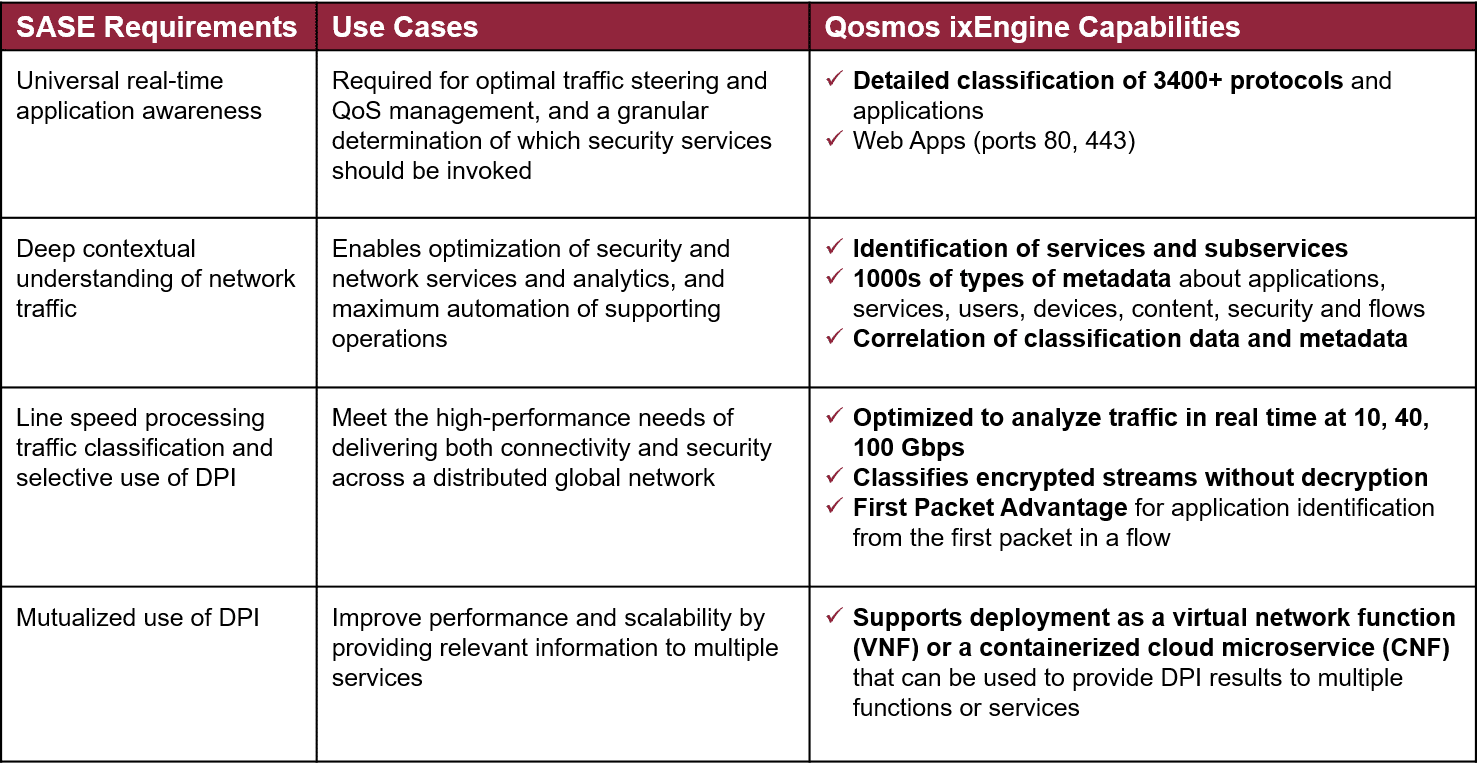
The table below summarizes how application classification is used in SASE, and which features of the Enea Qosmos ixEngine map to these use cases.
To learn more, visit the Enea Qosmos SASE webpage.