A New Way of Detecting TLS (SSL) MITM Attacks
What is a Man-in-the-Middle (MITM) Attack?
An MITM attack happens when a third party inserts themselves between a client (user) and server (application) and secretly intercepts all their communication flows. The main aim of MITM attacks is to steal sensitive data such as login credentials, bank account information, credit card information, etc., and they can be extremely harmful as well as costly to both consumers and companies.
MITM attacks are difficult to detect and often go unnoticed, so by the time the data breach is exposed, it is too late. The damage has been done. It is a situation that is especially critical for TLS MITM attacks because TLS is the encryption protocol used to secure almost 90% of web traffic today, and it is generally thought to be impermeable. For this reason, security operations devote fewer resources to detecting breaches in TLS communications. However, attack workarounds do exist and, unfortunately, TLS MITM is a dangerous reality.
What is TLS MITM?
As the name implies, TLS MITM focuses on communication over the TLS (formerly SSL) protocol, such as HTTPS traffic. There are several versions of TLS that co-exist. Some are deprecated, such as TLS 1.0, while others with known vulnerabilities, such as TLS 1.1, are still out there because web servers are rarely patched. The latest version, TLS 1.3, whose adoption represents approximately 65% of the top 1 million websites, is supposed to be impenetrable, but even this version has weak spots and is open to TLS MITM attacks.
How does TLS MITM work?
Let’s take a TLS MITM attack focusing on HTTPS traffic as an example. The attack is organized in two stages:
- Interception and eavesdropping
- Decryption and re-encryption
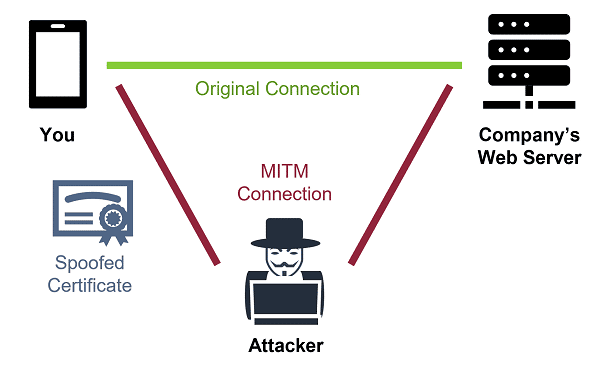
1) Interception and Eavesdropping
The simplest way for the attacker to intercept traffic is to set up a malicious, unsecured Wi-Fi hotspot that allows him or her to see all the unwitting victim’s communications. Another common method is to trick a device into redirecting a flow to a hacker through address manipulations like altering a flow’s Internet Protocol (IP) packet header (IP Spoofing), or corrupting an Address Resolution Protocol (ARP) exchange (ARP Spoofing), or editing Domain Name Server (DNS) records (DNS Spoofing or Proxy auto-config (PAC) Corruption). Misdirection via the Internet’s routing protocol, the Border Gateway Protocol (BGP), can also be used but is rare because it’s a much more complex type of attack perpetrated on a massive scale targeting a huge number of users at once. Often Internet Service Provider (ISP) collaboration/hijacking is needed to modify the BGP tables.
2) Decryption and Re-encryption
Once an attacker has received a victim’s data, the second stage is to access the user or server data without alerting either the sender or legitimate recipient. This is often achieved using an SSL/TLS Proxy to act like the server from the client’s standpoint and vice versa. An authentication certificate, specifically a custom root certified authority (CA) certificate, that is trusted by the victim’s browser is mandatory for this to work. This can be performed in several ways:
- Attackers can corrupt the legitimate custom root CA certificates that enterprises use within the legitimate proxy (MITM) set-ups required for performing cybersecurity functions like firewalling and data loss prevention (DLP).
- In some countries, ISPs have been known to prompt users to install custom root CA certificates as part of nationwide government-initiated Internet eavesdropping.
- Attackers can hack into victims’ computers and install third party custom root CA certificates. This can also be done by malware.
- Older versions of TLS can be subject to downgrade attacks such that vulnerabilities known in earlier versions (e.g. weak encryption) are exploited.
Why is it so important to detect MITM/TLS MITM attacks?
Data breaches are the principal aim of all MITM attacks, with the goal to steal personal data like login credentials and financial information. They can have huge direct and indirect financial consequences on companies including fines, lawsuits, etc. (c.f. IBM data breach report 2021).
Reputational damage following public exposure of a data breach can also have a significant impact as customers and consumers switch to alternative companies.
Some MITM attacks can be part of broader cyberbreach initiatives like advanced persistent threats (APT) which are attacks that can remain active on a network for a long time before discovery. The goal of APTs may be encrypting data for purposes of extortion, exfiltrating trade secrets, gaining control of key systems to disrupt business operations, or a host of other ends. In such cases, an MITM attack can be used to facilitate such breaches by gaining access to login credentials or inserting malware into intercepted flows.
MITM attacks, and particularly TLS MITM attacks due to TLS’s widespread use for communication security, therefore represent a huge risk to companies, posing a direct threat to both business and reputation. Detecting them as early as possible is essential.
A New Way of Detecting a TLS MITM Attack: the MITM Threat Score
The Enea Qosmos ixEngine® is a state-of-the-art next generation traffic visibility technology that uses several concurrent techniques to classify network traffic, applications and services while extracting and computing relevant metadata. These metadata can provide strategic information to cybersecurity operations, delivering contextual details that speed the detection of potential threats and enable much higher accuracy. This ability to extract specialized metadata makes the Enea Qosmos ixEngine particularly effective in detecting TLS MITM attacks. The product now performs calculations on select metadata in order to deliver a simple, yet highly accurate mechanism for estimating the likelihood of an MITM attack: The MITM Threat Score.
The MITM Threat Score indicates the probability of an event happening on a scale of 1-100. The calculation for the MITM Threat Score is based on numerous factors, among them:
- Round trip time (RTT) measurement
- Certification Authority (CA) reputation
- JA3 hashes
The score is computed for each new SSL/TLS connection.
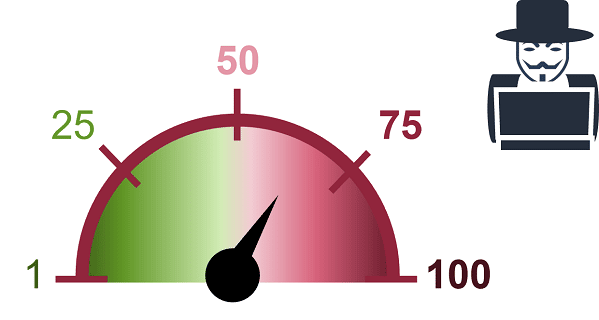
The MITM Threat Score – Scores Above 50 Indicate the Strong Possibility of an MITM Attack
The closer an MITM threat detection score is to 100, the higher the probability of MITM activity happening on the network, with anything over 50 worth investigating. However, lower scores can also be an indication of incoherencies in TLS connections and can be extremely useful in identifying weak spots in the current SSL/TLS deployments in a company’s infrastructure. All MITM metadata scores are therefore useful and should be investigated by a data analyst to help ensure that their organization is spared from the heavy damages an MITM attack can afflict.
Further Information
For more information on classification of encrypted traffic:
For more information on Enea Qosmos ixEngine:





