Detailed Traffic Visibility up to Layer 7 with Enea Qosmos Next-Generation DPI Engine
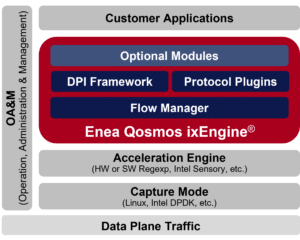
Enea Qosmos ixEngine® is a commercial grade, next-generation Deep Packet Inspection (NG DPI) and classification engine that recognizes over 4500 protocols and applications, more than any other Deep Packet Inspection (DPI) engine on the market.
Delivered as a Software Development Kit (SDK), it is composed of software libraries, modules and tools that are easily integrated into new or existing solutions. Developers of networking and security products benefit from market-leading traffic identification techniques and next-generation network intelligence technology to bring detailed, real-time traffic visibility to their solutions up to Layer 7.
Developed specifically for integration into 3rd party applications, Enea’s next-generation DPI engine, Qosmos ixEngine, removes the need to develop in-house protocol and application recognition capabilities, simplifying product development and accelerating delivery and time-to-market.
Product Overview
Enea Qosmos ixEngine: A Next-Generation DPI Engine
DATASHEET
Enea Qosmos ixEngine: Next-Generation DPI Engine for Maximum Traffic Visibility

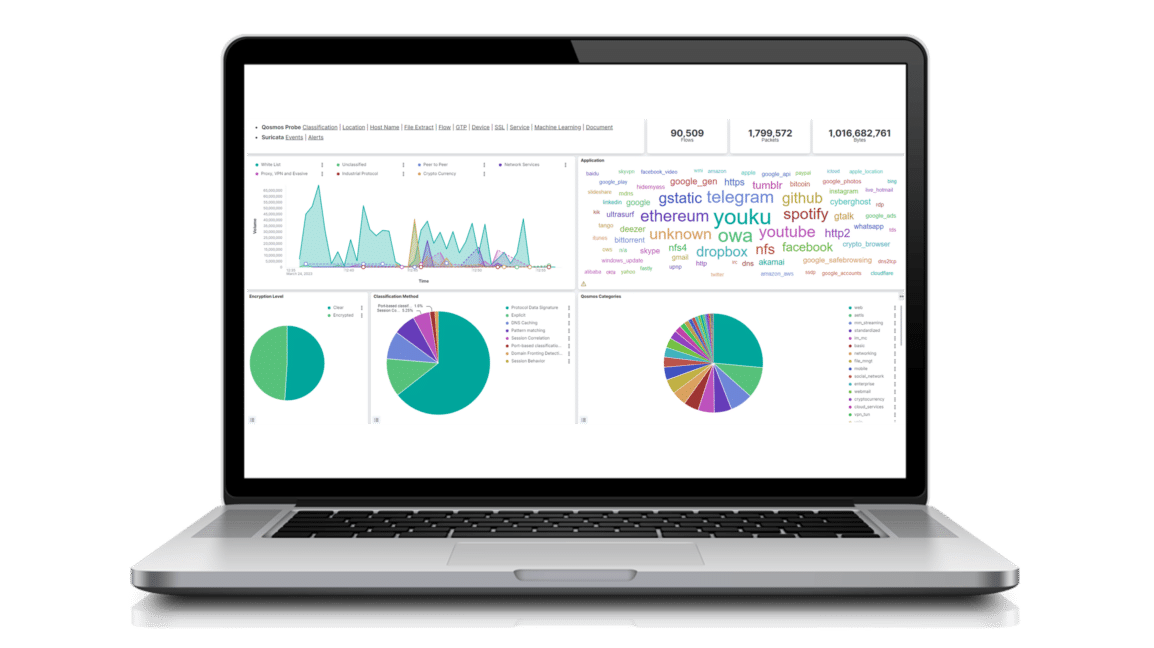
Enea’s next-generation DPI engine, Qosmos ixEngine, identifies over 4500 applications and protocols, more than any other on the market.

DATASHEET
Enea Qosmos ixEngine: Next-Generation DPI Engine for Maximum Traffic Visibility

Latest Resources and Industry Insights
Industry Recognition