The Most Deployed Embedded DPI Technology In Cybersecurity and Networking Solutions
With 75% market share, Enea Qosmos technology is the de facto industry standard for embedded Deep Packet Inspection (DPI) and Traffic Intelligence in cybersecurity and networking.
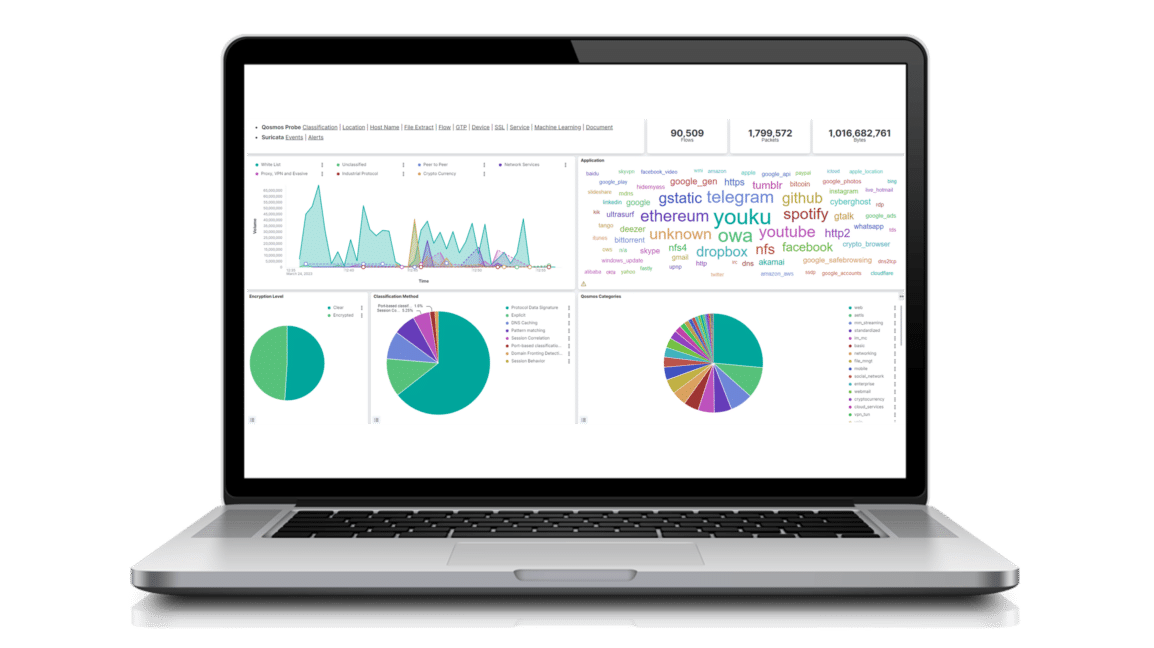
Our embedded deep packet inspection and traffic intelligence products classify traffic in real-time and provide granular information about network activities, boosting solution performance from the inside. Available as a next-generation DPI (NG DPI) and classification engine SDK or a standalone network sensor, they support an extensive range of protocols and applications and deliver detailed network traffic visibility, application awareness, and essential insights into encrypted traffic to cybersecurity and networking solutions such as SSE, SASE, SD-WAN, ZTNA, NGFW, IDS/IPS, and NDR/XDR.
Enea also offers IDS-based threat detection capabilities as an SDK, enabling easy and tight integration with cybersecurity solutions while remaining highly flexible and scalable.
Embedded DPI & Traffic Intelligence Products
Enea’s next-generation DPI engine, Qosmos ixEngine, identifies over 4500 applications and protocols, more than any other on the market.